A new variant of the information-stealing malware ViperSoftX has been discovered that targets a broader spectrum of applications, including the KeePass and 1Password password managers.
According to Trend Micro researchers, ViperSoftX now targets a greater number of cryptocurrency wallets, is capable of infecting browsers other than Chrome, and has begun to target password managers.
Lastly, the most recent version of the information-stealing malware includes enhanced code encryption and features to elude security software detection.
Targeting globally
ViperSoftX is malicious software that captures a variety of data from infected computers. It is also known that the malware installs a malicious Chrome extension called VenomSoftX.
In the most recent sample analyzed by Trend Micro, Firefox, Brave, Edge, and Opera are also targeted.
The malware was identified for the first time in 2020 as a JavaScript-based remote access trojan (RAT) and cryptocurrency hijacker. In November 2022, however, Avast reported that ViperSoftX was disseminating a much more potent variant.
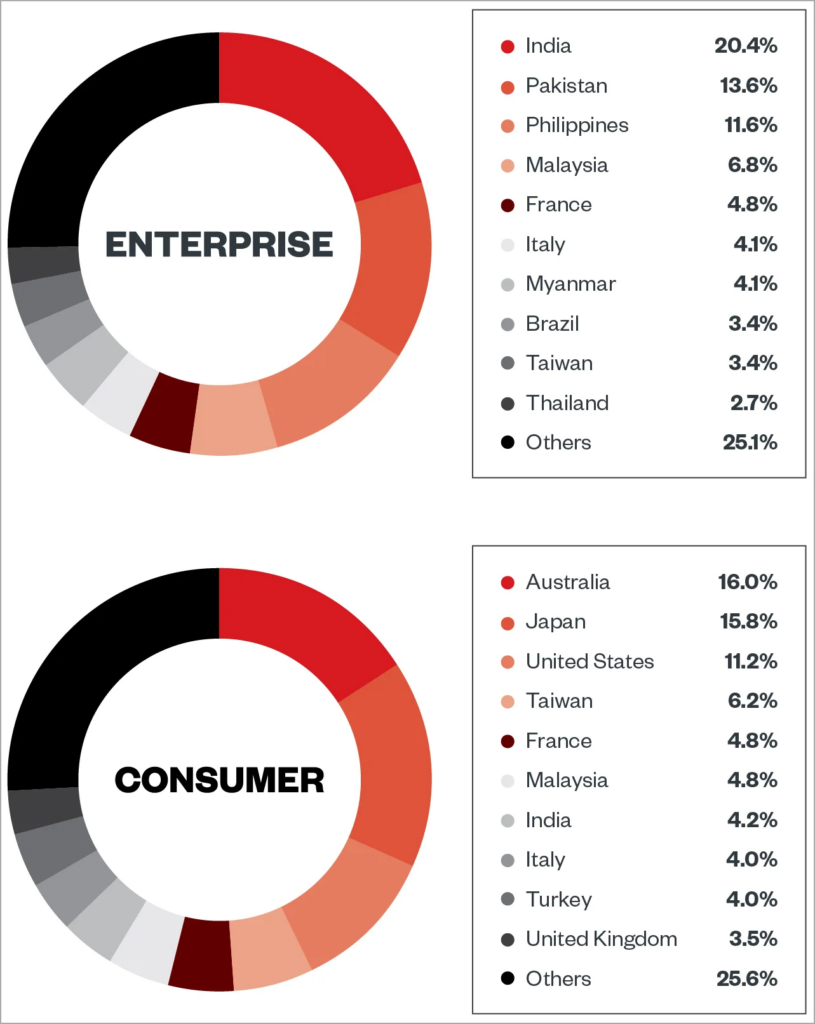
The majority of victims resided in the United States, Italy, Brazil, and India, according to Avast at the time.
This week, Trend Micro reported that ViperSoftX targets both consumers and businesses, with Australia, Japan, the United States, India, Taiwan, Malaysia, France, and Italy accounting for more than fifty percent of the detected activity.
According to the analysts’ observations, malware typically arrives as software exploits, activators, or key generators concealed within the software that appears to be benign.
Expanded objectives
In the version described by Avast, VenomSoftX targeted Blockchain, Binance, Kraken, eToro, Coinbase, Gate.io, and Kucoin wallets.
However, in the most recent variant, Trend Micro identified additional features that pilfer from the following additional wallets:
- Armory
- Atomic Wallet
- Binance
- Bitcoin
- Blockstream Green
- Coinomi
- Delta
- Electrum
- Exodus
- Guarda
- Jaxx Liberty
- Ledger Live
- Trezor Bridge
- Coin98
- Coinbase
- MetaMask
- Enkrypt
The analysts examined the malware to determine if it contained an exploit for CVE-2023-24055, which permits the retrieval of stored credentials in plaintext, but found no evidence of this exploit.
However, Trend Micro told BleepingComputer that if password managers are detected, it is conceivable that threat actors will target them with malicious activity in the later stages of the attack.
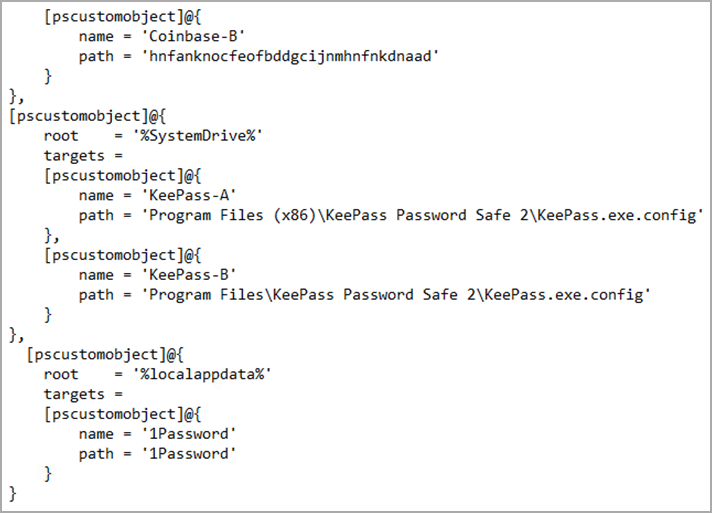
The KeePass section of the code was not present in reports from external researchers, so we know it is a later addition,” Trend Micro told BleepingComputer.
“However, it is only obvious that after collecting this information (wallets and password configuration), it will send it to its C2 if they exist.”
“We are examining the possibility of receiving back another set of codes/commands that would serve as remote functions in order to continue with further operations (since it has the potential to function like a backdoor)”
Enhanced safety
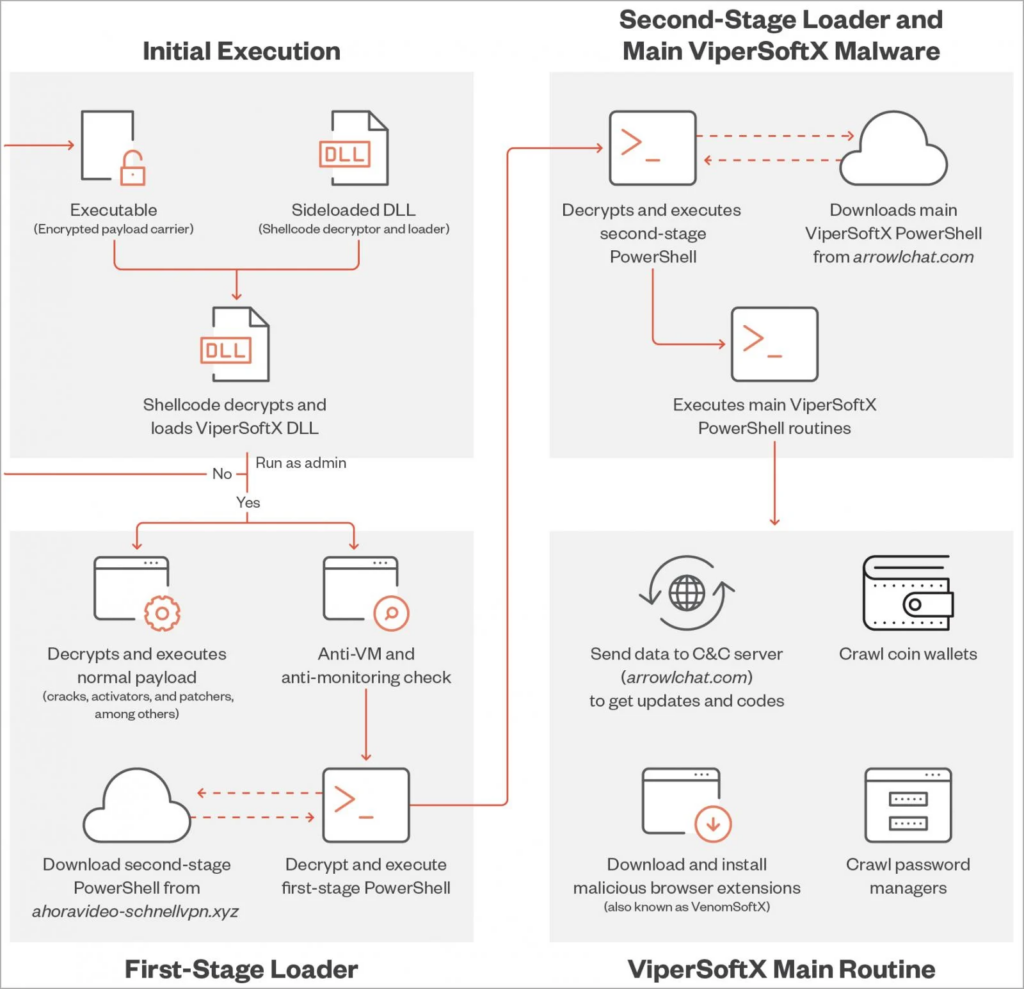
The new version of ViperSoftX employs multiple anti-detection, anti-analysis, and stealth-enhancing features, beginning with the use of DLL sideloading to execute on the target system within the context of a trusted process, thereby averting alarms.
Before initiating the infection procedure, the malware verifies the presence of certain virtualization and monitoring tools, such as VMWare or Process Monitor, and antivirus software, such as Windows Defender and ESET.
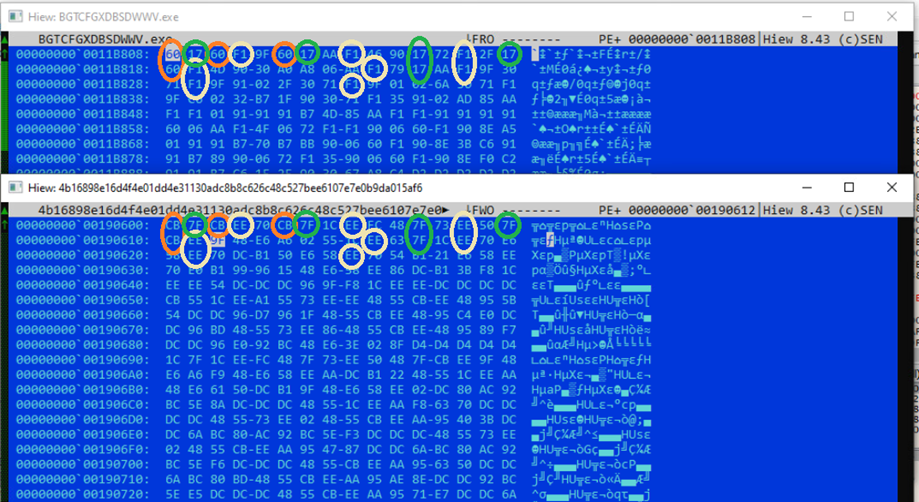
Most intriguing is the malware’s use of “byte mapping” to encrypt its code, which remaps the arrangement of shellcode bytes to make decryption and analysis much more difficult and time-consuming without the correct map.
“We have also found that each sideloader DLL has its own pair of executable and byte map, and a decryption attempt returns an incorrectly rearranged shellcode if used with another ViperSoftX-related executable,” Trend Micro explains in the aforementioned report.
This assures the shellcode cannot be decrypted without the correct DLL, which contains the correct byte map.
ViperSoftX introduces a new communication barrier for web browsers, making C2 infrastructure analysis and malicious traffic detection more difficult.

